11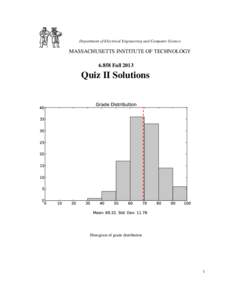 | Add to Reading ListSource URL: css.csail.mit.eduLanguage: English - Date: 2016-01-29 11:50:05
|
|---|
12 | Add to Reading ListSource URL: www.a-sit.atLanguage: English - Date: 2010-04-14 10:56:00
|
|---|
13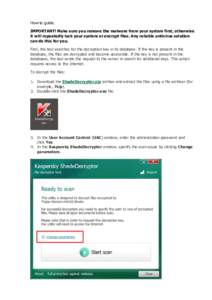 | Add to Reading ListSource URL: noransom.kaspersky.comLanguage: English - Date: 2016-07-25 08:15:55
|
|---|
14 | Add to Reading ListSource URL: nil.csail.mit.eduLanguage: English - Date: 2015-01-05 06:37:34
|
|---|
15 | Add to Reading ListSource URL: www.csuci.eduLanguage: English - Date: 2015-03-18 16:52:07
|
|---|
16 | Add to Reading ListSource URL: www.nro.govLanguage: English - Date: 2015-08-10 11:02:47
|
|---|
17 | Add to Reading ListSource URL: papi.rediris.esLanguage: English |
|---|
18 | Add to Reading ListSource URL: autotimesystems.co.ukLanguage: English - Date: 2016-07-12 03:22:31
|
|---|
19 | Add to Reading ListSource URL: www.faa.govLanguage: English - Date: 2015-12-28 09:31:39
|
|---|
20 | Add to Reading ListSource URL: papi.rediris.esLanguage: English - Date: 2007-10-13 04:03:53
|
|---|